From a not recognized "the ugly duckling" become the envy of everyone "White Swan", is ideal for every start-up. Help these start-up enterprises to solve security issues, better complete transformation to achieve the ideal, white hat meeting platform main service target of Hans Christian Andersen. Zhao said, "Anderson's name, a combination difficult to start a business, but the meaning of a happy future, and easy to remember. "
Anderson also ducklings in the platform's LOGO image.

Zhao, codenamed zwell
| Research and positioning
But at the beginning of project concept, platform services are not so clear. Platform technology is basically designed for large enterprises.
As vulnerability monitoring in large data technology technology traffic monitoring, workplace management technology in BAT, 360 corporate security protection, such as is common, but inappropriate for small and medium enterprises. Location is the Saas model and platform services, large enterprises are sensitive to public cloud services, and small and medium enterprises generally do not mind too much.
Big business is usually supported by a security team of about 200 people and start-ups because of an insufficient budget, experience, results in poor security, but the attack is inevitable. Zhao and his Group eventually decided that this security service mode of enterprise, copied to the small and medium enterprises, and provide a lower threshold for SMEs, but effective solutions to security problems in some way.
Although the entire project planning with nearly a year's time, but the demo from project start to finish, but only three months.
Platform's full name of Hans Christian Andersen, Andersen • enterprise platform threat perception. SANS Institute is the definition of threat information against security threats, threat, exploit, malware, vulnerability and hazard indicators, the data that is collected is used to assess the application of set. White hat meeting the definition of threat information is simple:
Who want to do you, who do you like, wherever possible threat to enterprise security threat intelligence.
Zhao told Lei feng's network (search for "Lei feng's network", public interest), usually enterprise on its own assets are not familiar with, after which leads to identify vulnerabilities and threats, and repair efficiency is very low.
There used to be a giant company, playing a patch with three day's time, because know enough about their assets.
Enterprise security threat intelligence for timely and accurate discovery, Andersen's platform of enterprise assets to make a comb, and fingerprints on the label.
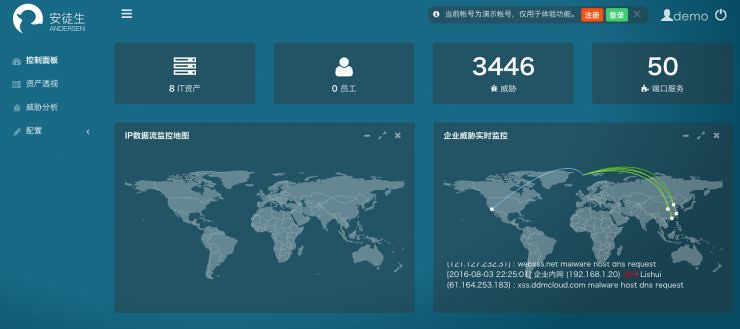
Anderson perspective platform assets page
Andersen's platform IT assets and employee assets corporate assets are divided into two parts.
Robotic devices in the enterprise, called IT assets, in addition to servers, laptops, printers, desktops, these physical assets, Web site operators can also belong to the enterprise IT asset management.
Personnel assets is the employee or customer information. For example, the staff will use registered mail accounts of other sites, once the other Web site services to be invaded, on disclosure of company information will also pose a threat.
So-called fingerprints tab is to calibrate the asset servicing.
As with human fingerprints, IT assets have fingerprints, like the device number, some vulnerabilities in enterprise security source assets and open some ports or services. Flawless 6s case
| Data come from
Threat information without data. Anderson, primarily through Noesec data security collaboration platform and social threat intelligence collection platform two channels to get information.
Prior to the development platform of Hans Christian Andersen, white hat meeting the creation of a Noesec data security collaboration platform. Platforms can take a business open to the public all of the fragmented enterprise asset information automated crawlers, accumulation, after forming a huge asset system.
Black underground Trade Center in the country is mainly forums and QQ groups, Andersen will monitor QQ by launching the white hat group and Forum data and timely information related to enterprise security threat gets to the service. Zhao says:
We will get hat from there first time to being trafficked, enterprise data and information, specific leak what data we do not know, but we also has a standard for access to information, we will take this data to communicate with the enterprise for a for businesses to identify for themselves. Flawless iPhone 6s plus case
Hui also had a white hat only for Http Protocol, Web application layer "global Web site". By collecting fingerprints of global Web services, you can easily identify a website on which ports, which Web Server to use, and which programming language, as well as what kind of open source frameworks (such as: CMS, etc). What is global online can also be found the Squid proxy server, which site using Jquery, what online H3C routers, which site uses GeoTrust certificates, website of a Trojan, which Web sites use the CloudFlare CDN.
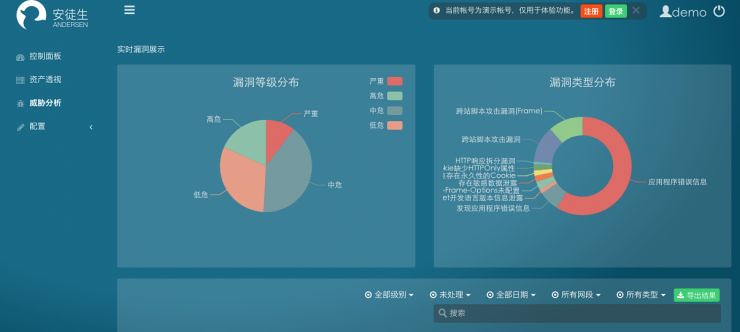
Anderson platform threat analysis page
Through the big Gets the data to enterprise threat intelligence information, Andersen's platform to analyze intelligence, to divide the vulnerability and is difficult to use for high risk, medium risk, low risk four levels, and provide repair advice.
| In a fairy tale real
Andersen platform demo now online through website forms, and try in some familiar companies and polished, then accepted try enterprise and industry practitioners make some adjustments and improvements. But Zhao believes that
White hat meeting at present product research and development progress is still too slow, although technical team has been expanded to 20 people, have some experience before, but the only one to fill in, rush.
While the cloud services model, you need powerful servers and bandwidth to support, which is a big cost.
As Anderson when the platform started to promote, Zhao said don't worry.
On one hand, product has not reached now a very good condition. As long as they can at this stage to provide the domain name, you can automate monitoring and threat information. But this is only an external threat intelligence, Enterprise probes of some traffic to the internal layout, this could be a very big bucket. Businesses will not accept, in what form to accept, need to discuss. Log analysis capabilities and I have not added features in the accumulation of machine learning.
Meanwhile, Andersen's platform of promotion and profit model and is also exploring. Only accredited does not mean willing to pay for your consumption. Although profit is not the ultimate goal, but is willing to spend on the product value of the performance.
Fight in security circles for many years, Zhao also has its own experiences, runs more quickly are likely to die sooner, step jogging, slow and steady is good.
No comments:
Post a Comment